
Advanced Data Protection: Next-Level Security for Your Digital Life
Updated: July 2025
The security of personal and organisational data has transcended basic antivirus software and firewalls, ushering in the need for advanced data protection. This evolving cybersecurity landscape demands more robust defence mechanisms to protect sensitive information from increasingly sophisticated cyber threats. Advanced data protection, including zero-trust data protection, offers a comprehensive approach to securing digital assets, ensuring that data remains safe, private, and accessible only to authorised users. Incorporating strategies such as Apple’s advanced data protection and iCloud’s advanced data protection further reinforces the security perimeter around the valuable data stored within these ecosystems, protecting it against unauthorised access and potential breaches.
Throughout this article, we will discuss the importance of advanced data protection in maintaining digital security, including encryption as the cornerstone of data security.
The Importance of Advanced Data Protection
Why Basic Security Measures Are No Longer Enough
In the context of modern digital threats, traditional security measures such as firewalls and antivirus software are proving insufficient. The cyberthreat landscape is not only vast but also dynamic, presenting new challenges that require more sophisticated defences, such as advanced data protection. Attackers continuously develop new methods to breach systems, often exploiting human psychology or emerging technologies. This evolution demands a shift from basic security protocols to more comprehensive, proactive measures that can preemptively counteract these threats.
The Evolving Threat Landscape
The variety of digital security risks now includes sophisticated phishing attacks using AI and machine learning, ransomware demanding payments in untraceable cryptocurrencies, and the insecure nature of IoT devices, which can compromise entire networks. Additionally, the rise of cryptojacking and negative SEO attacks demonstrates the adaptability and persistence of cybercriminals. These evolving threats underscore the critical need for advanced data protection strategies that are not only reactive but also predictive, enabling organisations to stay one step ahead of potential breaches.
The implications of these threats are severe, with the average cost of a data breach in the U.S. now exceeding $8 million, in addition to the potential loss of consumer trust and legal repercussions. This financial and reputational damage can be particularly devastating for mid-sized businesses, which often lack the robust cybersecurity infrastructures of larger corporations but possess more valuable assets than small enterprises.
New strategies should be considered as cybersecurity attacks become increasingly serious. These strategies must be adaptable, continuously updated, and capable of addressing not only current but also emerging threats. This proactive approach is essential for maintaining the integrity and confidentiality of sensitive information in a world where cyber threats are becoming more intelligent and coordinated.
Essential Tools for Enhancing Your Digital Security
Antivirus Programs
Antivirus software plays a crucial role in digital security by protecting devices against malware, ransomware, and phishing attacks. Top-rated antivirus programs like Norton 360, Bitdefender Antivirus Plus, and McAfee offer comprehensive protection. These programs not only detect and remove malicious software but also provide real-time protection to prevent new threats from compromising your digital safety. For instance, Norton 360 is highlighted for its overall effectiveness and additional features like identity theft monitoring.
Firewalls
Firewalls serve as a fundamental barrier between trusted internal networks and potential external threats. They monitor and control incoming and outgoing network traffic based on predefined security rules. Various types of firewalls, including packet filtering, stateful inspection, and next-generation firewalls, cater to different security needs. For example, stateful inspection firewalls track the state of active connections and make decisions based on connection state and context, offering enhanced security for medium to large enterprise networks.
Identity Theft Protection
Identity theft protection services are essential in protecting personal and financial information online. Services like Aura and LifeLock monitor your personal data, alerting you to potential misuse, and provide tools for recovery if your identity is compromised. These services typically include features like credit monitoring, dark web surveillance, and alerts on suspicious transactions, which are vital in today’s digital age where personal data can be easily accessed or stolen.
By leveraging these kinds of tools, individuals and organisations can significantly enhance their digital security, ensuring that their sensitive data remains protected against the evolving landscape of cyber threats.
Encryption: The Cornerstone of Data Protection
What is Encryption
Encryption is the process of converting data into a coded format that can only be accessed by those who possess the correct decryption key. This process ensures the confidentiality and integrity of the data by making it unreadable to unauthorised parties. The key to decrypting the encrypted data must be known; otherwise, the data remains inaccessible and unusable.
Types of Encryption
There are two primary types of encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encrypting and decrypting data. This method is faster but requires that both the sender and receiver have access to the same key, which can pose challenges in key distribution and security.
Asymmetric encryption, also known as public key cryptography, utilises a pair of keys – one public and one private. The public key is used for encryption, while the private key is used for decryption. This method allows for secure data transmission even if the encryption key is publicly known, as the private key remains confidential.
How to Implement Encryption
Implementing encryption involves several steps to ensure data security effectively:
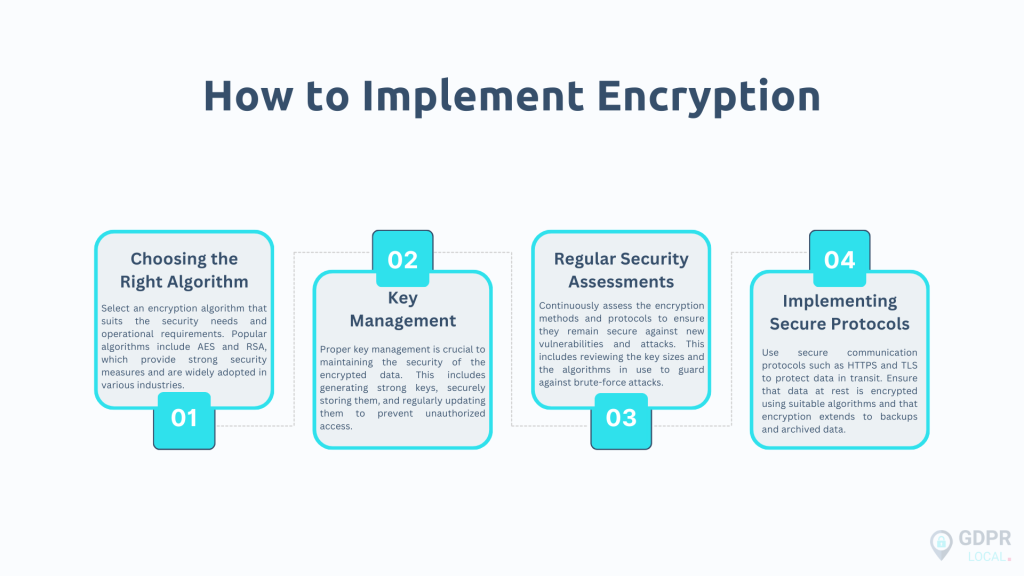
By following these steps, organisations can effectively implement encryption to protect sensitive information from unauthorised access and cyber threats.
Best Practices for Maintaining Digital Security
Regular Software Updates
Software updates play a vital role in fortifying digital defences by addressing security vulnerabilities and introducing enhancements to counteract emerging threats. It is essential to install these updates promptly to prevent cyber attackers from exploiting known vulnerabilities. Regular updates ensure that all systems are equipped to handle the latest security challenges, significantly reducing the risk of successful breaches.
Strong Passwords and Two-Factor Authentication
The foundation of individual online security is the creation and maintenance of strong, unique passwords combined with the implementation of Two-Factor Authentication (2FA). Strong passwords act as the first line of defence against unauthorised access, making it challenging for attackers to breach accounts. Two-factor authentication adds an additional layer of security, requiring a second form of verification beyond just the password, which effectively blocks 99.9% of automated attacks. Utilising a password manager can enhance this process by generating and managing complex passwords, thus bolstering security with convenience and efficiency.
Regular Data Backups
Implementing a robust data backup strategy is crucial for any organisation to mitigate the risks of data loss due to system failures, cyberattacks, or other disasters. Regular backups not only ensure the availability of data for recovery but also support business continuity. It is recommended to automate backups to maintain consistency and reliability. Testing and monitoring of these backups are essential to ensure their effectiveness in real-time recovery scenarios. This practice not only secures data but also supports regulatory compliance and enhances consumer trust by demonstrating a commitment to data security.
Conclusion
Given the multifaceted challenges and potential implications of cyber threats, the significance of adhering to advanced data protection strategies cannot be overstated. The evolving nature of cyberattacks calls for a proactive and adaptive approach to digital security, emphasising the integration of advanced protection measures, regular system updates, the use of strong, unique passwords, and the importance of regular data backups.
The journey toward securing one’s digital existence is ongoing, and we strive to offer valuable insights and promote an environment where security is paramount and awareness and preparedness are key.
FAQs
Is it advisable to activate advanced data protection on my iPhone?
Yes, if you are seeking the highest level of security and privacy, activating Advanced Data Protection (ADP) is recommended. However, it’s important to establish alternative methods for account recovery, as Apple will not be able to assist in unlocking your encrypted files if you lose access to your account.
Is it possible for Apple to disable advanced data protection?
Yes, you can disable Advanced Data Protection at any time. To do this, go to the Settings on your iPhone or iPad, tap your name, then tap iCloud, and finally scroll down to disable Advanced Data Protection. This action securely uploads the necessary encryption keys to Apple’s servers, reverting your account to standard data protection.
How do security keys differ from advanced data protection in iCloud?
The main difference lies in the level of security. While iCloud encryption involves securing encryption keys in Apple’s data centres to facilitate data recovery and only end-to-end encrypts certain data, Advanced Data Protection for iCloud provides a higher level of cloud data security by offering additional encryption measures.
Why might I be unable to activate advanced data protection?
If you are unable to activate Advanced Data Protection, it may be due to restrictions on one of your devices linked to your Apple ID. The onscreen instructions might provide further details, or you may need to remove the problematic device from your Apple ID device list to proceed with the activation.