Comparing DPIA Requirements Across Global Jurisdictions
Updated, June 2025
Recent statistics reveal staggering data protection challenges – over 4.1 billion records compromised during 2023’s first half alone. Data Protection Impact Assessments (DPIAs) emerge as critical safeguards against such breaches, enabling organizations to proactively identify and mitigate data protection risks before costly incidents materialize.
Modern privacy compliance demands sophisticated understanding of varied DPIA requirements. Regulatory frameworks differ substantially between GDPR jurisdictions, Asia-Pacific regions, and the Americas. Let’s explore the differences.
Key Takeaways
DPIAs Are Essential Across Global Privacy Frameworks
Data Protection Impact Assessments (DPIAs) are critical for identifying and mitigating privacy risks, with mandatory requirements under GDPR and increasing obligations across Asia-Pacific and U.S. state laws.
Jurisdictional Requirements Vary Significantly
While the EU mandates detailed, rights-focused DPIAs, jurisdictions in the Asia-Pacific and the Americas differ in scope and enforcement, requiring flexible, multi-jurisdictional strategies for compliance.
Effective DPIAs Require Structured, Documented Methodologies
A compliant DPIA includes defined steps: documenting processing activities, assessing necessity and risk, implementing mitigation measures, and maintaining dynamic review protocols—all supported by staff training and suitable technology tools.
Fundamentals of Data Protection Impact Assessments (DPIAs)
Data Protection Impact Assessments represent cornerstone compliance mechanisms within modern privacy frameworks. Professional organizations must master these fundamental concepts to ensure regulatory adherence and risk mitigation effectiveness.
What is a Data Protection Impact Assessment
Data Protection Impact Assessments constitute systematic evaluation protocols designed to identify, assess, and minimize privacy risks within organizational data processing activities. DPIA frameworks extend beyond mere compliance requirements, establishing risk management mechanisms that protect individual privacy rights and organizational interests through continuous evaluation processes.
Key Components of an Effective DPIA
Professional DPIA frameworks mandate inclusion of specific critical elements:
• Systematic processing operation documentation and purpose specification
• Comprehensive necessity and proportionality analysis
• Detailed rights-based risk evaluation protocols
• Strategic risk mitigation measures
• Stakeholder consultation documentation requirements
When are DPIAs Required
Regulatory frameworks mandate DPIA implementation under specific high-risk processing scenarios.
Mandatory assessment triggers include:
1. Systematic and Extensive Profiling: Automated processing operations generating decisions with significant individual impact
2. Large-scale Processing: Operations involving special category data or criminal conviction information
3. Public Monitoring: Large-scale systematic monitoring of public spaces
Professional organizations should consider implementing DPIAs for all substantial data processing initiatives, regardless of mandatory requirements. This strategic approach enables early risk identification and cost-effective mitigation strategies.
Regulatory consequences for DPIA non-compliance include fines of up to £8.7 million or 2% of global annual turnover, whichever proves greater. However, DPIA implementation delivers substantial value beyond compliance, establishing stakeholder trust and demonstrating organizational commitment to data protection excellence.
Global DPIA Requirements
Global DPIA requirements demonstrate significant jurisdictional variations, necessitating sophisticated compliance strategies for multinational organizations.
European Union (GDPR) Standards
GDPR establishes authoritative DPIA standards through Article 35, mandating comprehensive assessments for high-risk processing operations affecting individual rights and freedoms.
Regulatory compliance demands rigorous documentation encompassing:
• Detailed processing operation specifications
• Thorough necessity and proportionality evaluations
• Comprehensive risk assessment protocols
• Structured stakeholder consultation records
Asia-Pacific Regional Requirements
Asia-Pacific jurisdictions present distinct regulatory variations. Currently, four primary jurisdictions – Singapore, South Korea, China, and the Philippines maintain mandatory DPIA protocols. Chinese PIPL legislation establishes stringent requirements for sensitive data processing and cross-border transfers.
Regulatory expansion continues with Vietnam’s recent implementation of mandatory DPIA submissions to governmental authorities. Regional frameworks demonstrate notable divergence from European standards, with numerous jurisdictions adopting flexible assessment approaches.
Americas Regulatory Framework
Americas jurisdictions exhibit dynamic regulatory evolution. United States federal requirements, established through the eGovernment Act of 2002, primarily govern public sector operations. Private sector obligations emerge through state-level initiatives, with eleven jurisdictions implementing explicit assessment requirements.
California legislation mandates annual cybersecurity evaluations for high-risk processing operations. Colorado regulations prohibit elevated-risk processing activities absent documented impact assessments. These requirements demonstrate increasing regulatory sophistication across state jurisdictions.
Risk Assessment Methodology
Professional risk assessment protocols demand sophisticated methodological frameworks. Regulatory compliance requires systematic approaches to privacy risk identification, evaluation, and mitigation within organizational data processing operations.
Identifying Privacy Risks
Risk identification protocols necessitate comprehensive examination of potential privacy threats.
Professional assessment frameworks identify critical risk categories:
| Identity theft and fraudulent activities | Financial compromise scenarios | Reputational integrity breaches | Physical security threats |
| Confidentiality violations | Discriminatory outcomes | Personal data control compromises |
Evaluating Impact Severity
Professional impact assessment protocols incorporate dual-factor analysis methodologies, evaluating both probability metrics and severity indicators. Critical evaluation parameters encompass data sensitivity levels, affected population scope, and rights impact magnitude.
Risk classification frameworks recognize elevated threat levels through multiple vectors:
| Privacy rights exercise impediments | Social disadvantage manifestations | Pseudonymization compromise scenarios | Economic impact considerations |
Mitigation Strategies
Professional mitigation frameworks emphasize pragmatic, resource-efficient risk management protocols. Strategic implementation encompasses multiple protective layers:
Primary measures mandate data minimization principles and strict retention protocols. Secondary safeguards incorporate advanced technological security implementations and comprehensive personnel training programs. Tertiary protection mechanisms establish robust data-sharing governance and enhanced privacy notification systems.
Risk mitigation documentation requires maintained protection registers tracking identified threats and corresponding countermeasures. Dynamic documentation protocols enable continuous effectiveness monitoring and strategic adaptation capabilities.
Professional risk management frameworks acknowledge complete risk elimination remains impractical. Strategic objectives focus on risk reduction to acceptable tolerance levels through sophisticated safeguard implementations. Structured methodological approaches ensure optimal balance between privacy protection imperatives and operational efficiency requirements.
Implementation Framework
Professional DPIA implementation demands sophisticated operational frameworks. Successful deployment requires structured methodologies combined with dynamic review protocols and comprehensive documentation standards.
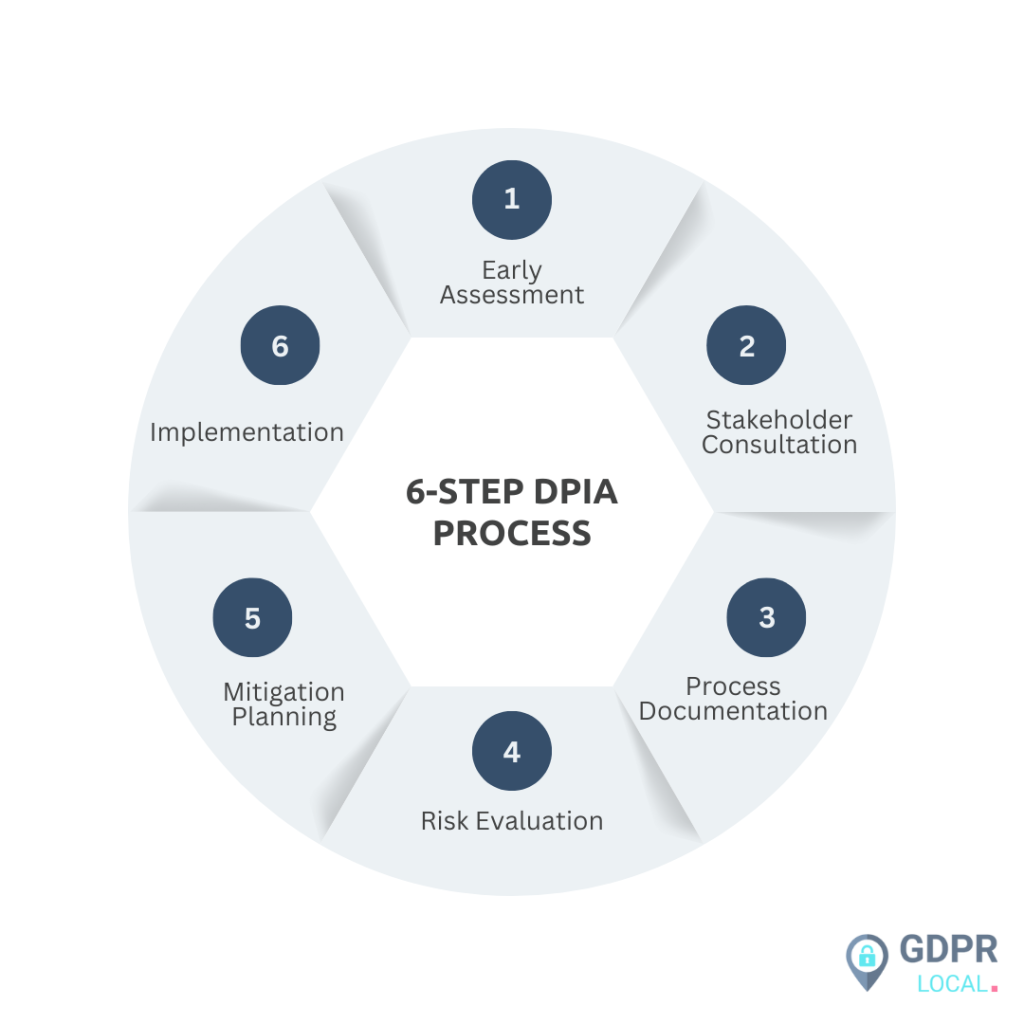
Step-by-Step DPIA Process
Professional implementation frameworks mandate systematic execution protocols:
Documentation Requirements
Regulatory compliance mandates comprehensive documentation protocols.
Professional documentation frameworks require:
• Detailed processing operation specifications
• Necessity and proportionality analysis documentation
• Risk evaluation and mitigation protocols
• Stakeholder engagement records
• Protection officer recommendations
• Implementation timeline matrices
Standardized documentation templates ensure systematic compliance adherence. Template customization protocols must reflect organizational requirements while maintaining regulatory standards.
Review and Update Procedures
Professional frameworks recognize DPIAs as dynamic compliance instruments.
Strategic review protocols encompass:
Routine Reviews: Systematic effectiveness evaluations triggered by significant processing modifications.
Change Triggers: Assessment updates necessitated by technological implementations, purpose modifications, or emerging risk identification.
Documentation Updates: Continuous documentation maintenance recording modifications, determinations, and strategic rationale.
Framework implementation enables robust protection protocols while ensuring regulatory adherence. Protection Officer consultation remains critical throughout assessment processes, providing authoritative guidance for comprehensive DPIA execution.
Compliance Best Practices
Professional DPIA compliance demands good implementation strategies. Organizational growth requires strategic deployment of standardized templates, advanced technological solutions, and comprehensive personnel development programs.
Creating DPIA Templates
Professional template frameworks establish standardized assessment protocols adaptable across diverse processing operations. Effective template architectures mandate systematic documentation encompassing operational specifications, risk evaluations, and mitigation strategies.
Technology Tools and Solutions
Modern compliance frameworks leverage sophisticated automation capabilities. CNIL’s PIA software platform delivers intuitive interface capabilities supporting rapid risk visualization. Open-source architecture enables customized implementations within existing technological ecosystems.
Strategic technological deployment delivers multiple operational advantages:
• Automated assessment distribution mechanisms
• Centralized documentation control systems
• Streamlined evaluation workflows
• Enhanced stakeholder collaboration platforms
Staff Training and Awareness
Training excellence demands integration of jurisdictional requirements and sector-specific compliance obligations. Documentation protocols require comprehensive completion records and systematic competency verification procedures.
Protection officer roles necessitate advanced professional development frameworks beyond standard training protocols. Continuous education ensures authoritative command over evolving protection requirements and emerging compliance standards.
Strategic compliance frameworks mandate regular evaluation and enhancement of templates, technological solutions, and training methodologies. Proactive enhancement protocols ensure sustained regulatory adherence while strengthening stakeholder confidence.
Conclusion
Data Protection Impact Assessments constitute fundamental safeguards within modern privacy protection frameworks. Professional analysis demonstrates their critical role in risk identification and mitigation across global regulatory landscapes.
Jurisdictional DPIA requirements exhibit significant variation – European frameworks mandate structured approaches while Asia-Pacific regions demonstrate emerging regulatory sophistication. American requirements continue to evolve rapidly through state-level initiatives. These diverse frameworks necessitate sophisticated, adaptable assessment methodologies.
Professional implementation frameworks, incorporating systematic risk evaluation protocols and robust documentation requirements, enable comprehensive privacy protection programs. Strategic deployment of these methodologies ensures sustained regulatory compliance across diverse jurisdictional requirements.
Need assistance with conducting a DPIA? Our team is ready to help you. Contact us at [email protected].
FAQs
1. When is a Data Protection Impact Assessment (DPIA) required?
A DPIA is required for high-risk data processing activities, such as large-scale profiling, processing of sensitive data, or public monitoring. However, organisations are encouraged to conduct DPIAs for all substantial processing to identify risks early.
2. Do DPIA requirements differ by country?
Yes. GDPR mandates detailed DPIAs, while Asia-Pacific countries like China and Singapore have emerging but varied standards. In the U.S., DPIA-like assessments are being developed at the state level, such as in California and Colorado, particularly for high-risk processing.
3. What should be included in a DPIA?
A DPIA should document the processing purpose, assess necessity and proportionality, identify risks to individuals, outline mitigation strategies, and include records of stakeholder consultation and review procedures.