
Enterprise Data Protection: Securing Large-Scale Information Assets
Cyber threats and regulatory pressures have made it necessary for businesses around the world to safeguard large-scale information assets. Corporate, company, and business data protection strategies are not just about compliance; they are a cornerstone of trust and reliability in today’s market. The intricacies of protecting sensitive information while ensuring accessibility and efficiency demand a sophisticated approach, combining technological innovation with strategic foresight.
As a roadmap for businesses to protect their information assets against emerging threats and vulnerabilities, this piece guides readers through the complexity of the topic.
Why Enterprise Data Protection is Crucial
Enterprise data protection is not merely a technical requirement but a strategic necessity that impacts various facets of business operations.
Financial Implications
The financial stakes of inadequate data protection are alarmingly high. Non-compliance with data protection regulations such as the GDPR or CCPA can result in severe penalties. For instance, businesses could face fines up to €20 million or 4% of their annual global turnover under the GDPR. Moreover, the aftermath of a data breach extends beyond fines, encompassing legal fees, investigation costs, and compensations, which collectively can exacerbate the financial burden. Additionally, data breaches typically increase customer churn by about 4%, directly affecting both current and future revenue streams.
Reputation Management
The impact of a data breach on an enterprise’s reputation can be devastating and long-lasting. Surveys indicate that 60% of consumers would likely cease doing business with a company that has experienced a breach involving personal information. The loss of consumer trust translates directly into a decline in business, making reputation management a critical component of enterprise data protection strategies. Effective data protection practices not only prevent potential financial losses but also help in maintaining and enhancing customer trust and loyalty.
Legal Obligations
Legal compliance is the cornerstone of enterprise data protection. Organizations are mandated to adhere to stringent data protection laws, such as GDPR and HIPAA, which are designed to safeguard consumer privacy and data integrity. Failure to comply can lead to significant legal consequences including fines and penalties. However, compliance should not be viewed merely as a legal deterrent but as an opportunity to reinforce data governance and enhance overall business integrity.
The importance of data protection is clear: it is a comprehensive strategy that supports not only legal and financial aspects but also contributes significantly to maintaining and growing customer trust and business reputation.
Key Technologies in Data Protection
Encryption Software
Encryption software plays a pivotal role in safeguarding data by rendering it unreadable without the appropriate decryption key. This technology is essential for protecting sensitive information against unauthorized access and theft. Among the leading solutions, AxCrypt stands out for its user-friendly approach, utilizing a strong master password and the AES encryption algorithm to secure files seamlessly. Similarly, NordLocker provides encrypted storage containers that offer full access when open but secure data when locked, making it an ideal choice for cloud-based file sharing.
Network Security Tools
Network security tools are crucial for monitoring and protecting an organization’s IT infrastructure. These tools provide comprehensive visibility into network traffic, enabling the detection and prevention of potential security threats. AlgoSec, for instance, automates network security policy management, ensuring that firewalls and routers are configured correctly to protect against misconfigurations that could lead to severe security breaches. Additionally, tools like Wireshark and Nexpose offer capabilities for real-time data capture and vulnerability scanning, respectively, enhancing the overall security posture of the network.
Data Loss Prevention Systems
Data Loss Prevention (DLP) systems are integral to preventing sensitive data from leaving the corporate network without authorization. Cyberhaven’s solution integrates cloud and endpoint DLP capabilities, offering real-time detection of sensitive data exposure and user activities leading to potential data breaches. On the other hand, Proofpoint provides a comprehensive DLP platform that includes cross-channel data loss prevention, insider threat management, and web security, all managed from a cloud-based dashboard. These systems are designed not only to protect against data leaks but also to enforce data security policies effectively, ensuring compliance with regulatory standards.
Building a Culture of Security
Employee Awareness Programs
In 2024, the digital landscape witnessed over 5,000 data breaches, exposing more than 30 million records, largely due to inadequate employee training in cybersecurity best practices. This underscores the critical need for security training programs that transform employees from potential security risks to the organization’s greatest assets. Such programs should emphasize the role of employees in safeguarding data and include training on adhering to company security policies, maintaining strong passwords, securing assets, and regularly updating software.
Interactive elements like quizzes and real-world scenarios can significantly enhance the effectiveness of these programs by engaging participants and reinforcing learning objectives. Moreover, providing resources such as reference materials and support contacts is essential for ongoing learning and adherence to data protection protocols.
Leadership Involvement
A security-first mindset must start from the top, where leaders not only support the security team but also actively participate in security initiatives. By setting an example in security practices, leaders can instill a culture of security throughout the organization. This includes direct involvement in hiring security talent, allocating funds for cybersecurity programs, and demonstrating a commitment to security in their daily activities.
Furthermore, leaders should ensure open communication channels within the organization, allowing employees to report issues and interact with IT and security departments without hesitation. This approach helps to foster an environment where security is seen as a collective responsibility.
Security-First Mindset
Adopting a security-first mindset is essential for embedding security into every aspect of organizational processes. This mindset involves viewing security as integral to all business operations and ensuring that every employee understands their role in maintaining security. Organizations with a security-first approach continually seek ways to enhance their security measures and create a unified effort towards safeguarding data.
Implementing such a mindset requires thoughtful investment in training and resources that promote inclusivity and psychological safety, enabling employees to confidently contribute to the organization’s security efforts. Best practices like consistently acknowledging employees’ contributions to security and engaging executive leadership in security discussions are crucial for advancing a proactive security posture.
Measuring the Effectiveness of Data Protection Efforts
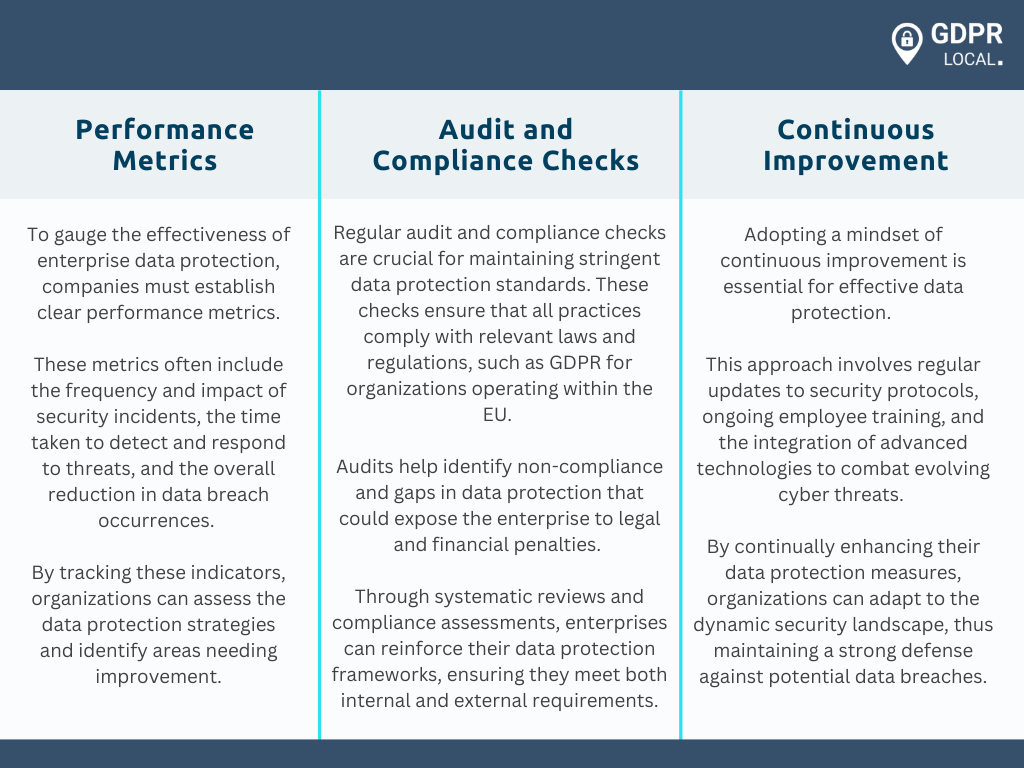
Conclusion
The journey through understanding the integral role of enterprise data protection concludes with the acknowledgment that continuous improvement and measurement of effectiveness are essential. Performance metrics, audit, and compliance checks, along with an unwavering commitment to enhancement, ensure that organizations can stay ahead of emerging threats and vulnerabilities. The broader implications of these efforts cannot be overstated; they extend beyond mere compliance to shape a secure, resilient corporate landscape where trust and reliability lead to sustained growth and success.
In keeping with the drive for clarity and the delivery of value-packed content throughout this article, these concluding thoughts aim to remind readers of the perpetual relevance and necessity of prioritizing data protection at every organizational level.
FAQs
What strategies can organizations employ to ensure their vast data stores are both secure and accessible?
To secure and maintain accessibility of large data volumes, organizations should utilize database accessibility monitoring tools or solutions. These tools help enhance security, detect and prevent unauthorized access or breaches, and uphold data integrity. Additionally, it’s crucial to guard against the risk of external cyber-attacks.
What are the steps to safeguard information assets in an organization?
Protecting information assets involves several critical steps:
– Identifying the assets
– Analyzing the risk of potential attacks
– Establishing a comprehensive security policy
– Implementing defensive measures
– Continuously monitoring these defenses.
What does enterprise data protection entail?
Enterprise data protection is the process through which security is administered, managed, and monitored across all data storages and objects under an organization’s control.
How can information be safeguarded at the enterprise level?
To ensure information security at the enterprise level, organizations should:
– Assess and determine the value of their information
– Manage the information throughout its lifecycle
– Opt for an appropriate enterprise mobility model
– Utilize external information systems securely
– Establish a system for compliance monitoring.