
Personal Data Protection: Safeguarding Your Digital Identity
The vast expansion of the internet and the proliferation of digital communication have indeed transformed the way society operates, but they have also introduced significant risks to individual privacy and security. Personal data protection is no longer a mere suggestion; it is a necessity in protecting one’s digital identity against unauthorized access, misuse, or theft. As regulatory frameworks evolve and cyber threats become more sophisticated, understanding and implementing user data protection measures is a must for individuals and organizations alike.
This article aims to explore the depths of personal data protection, offering insights into the essential steps individuals can take to protect their digital identities.
What is Personal Data Protection?
Definition and Importance
Personal data protection is mentioned in the EU Charter of Fundamental Rights, emphasizing the intertwining of data protection with other fundamental rights such as freedom of speech and assembly. Since the enactment of the General Data Protection Regulation (GDPR) in May 2018, it has become imperative for organizations within the European Economic Area (EEA) to ensure data protection measures are in place. Non-compliance can lead to severe financial penalties, potentially as high as 20 million euros or 4% of the annual turnover of the organization.
Organizations recognized for diligent data protection practices are more likely to retain customers and enhance their public reputation.
Common Threats to Personal Data
The landscape of data security is fraught with various threats ranging from cyber-attacks to human errors. Malware, a prevalent form of cyber threat, includes viruses, worms, spyware, and ransomware, which disrupt computer operations and compromise data integrity. Phishing attacks, another common threat, manipulate users into divulging sensitive information through deceptive emails or websites.
Data breaches can occur due to numerous factors such as hacking, which is now a lucrative industry for cybercriminals. These breaches often result in unauthorized access to sensitive personal and financial information. Additionally, physical threats like natural disasters or theft can also lead to significant data loss, highlighting the importance of comprehensive security measures that include both digital and physical safeguards.
To counter these threats, organizations must implement advanced security technologies and processes. This includes the use of encryption for data at rest and in transit, regular security audits, and the promotion of cybersecurity awareness among employees to prevent inadvertent data leaks.
Steps to Protect Your Digital Identity
To secure your digital identity effectively, it is crucial to adopt a series of proactive strategies.
Use Strong, Unique Passwords
Creating strong and unique passwords is foundational to personal data protection. A strong password should be at least 12 characters long, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using common words, pet names, or easily guessable combinations. Each account should have a distinct password to prevent a single breach from compromising multiple accounts. Consider using a password manager to maintain and manage these passwords securely. Password managers not only store your passwords but also help in generating strong passwords that are difficult to crack.
Enable Two-Factor Authentication
Two-factor authentication (2FA) significantly enhances account security by requiring two forms of identification before access is granted. This method combines something you know (like a password) with something you have (such as a mobile device) or an inherent characteristic (like a fingerprint). By enabling 2FA, you add an additional layer of defense, which helps protect your accounts even if your password is compromised. Various methods of 2FA include SMS codes, email verification, authenticator apps, and hardware tokens. It is advisable to choose the method that best suits your security needs and convenience.
Be Cautious with Sharing Information Online
When engaging with social media or any online platform, it is vital to be mindful of the information you share. Posts that seem harmless, like those about your favorite pet or the street you grew up on, can inadvertently provide answers to security questions and lead to data breaches. Always question the necessity of providing personal information before sharing it online. Is it essential for a quiz to know your full name, or for a website to have your home address if it isn’t delivering anything to you? Limit the sharing of sensitive information and ensure that you are interacting with trustworthy platforms.
These measures are not only practical but essential in the current digital landscape where data breaches and identity theft are rampant.
Tools and Applications for Data Protection
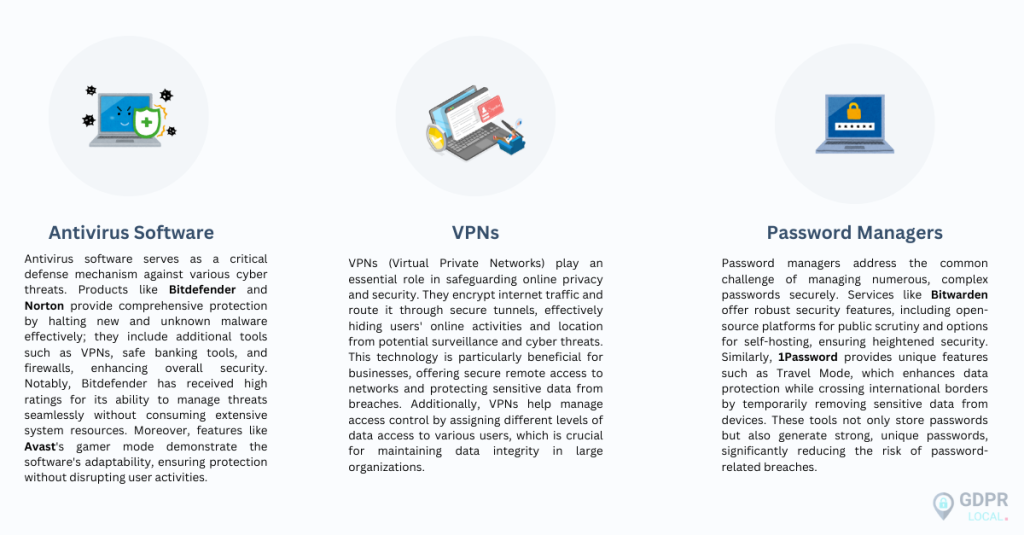
What to Do If Your Data Is Compromised
Identify Signs of a Data Breach
Detecting a data breach promptly is crucial to mitigate its impacts. Malicious actors often strive to conceal their activities, making early detection challenging. Regular system checks and monitoring for unusual activities are essential. Signs of a breach may include unexpected financial transactions, unfamiliar files on the system, or alerts from security tools.
Steps to Take Immediately
Once a data breach is identified, swift action is necessary:
| Secure Affected Systems | Immediately isolate and secure affected systems to prevent further data loss. Do not turn off affected machines until forensic experts can review them, as this may preserve crucial evidence. |
| Engage a Forensics Team | Employ a data forensics team to determine the breach’s scope and origin. This team will help in capturing forensic images of affected systems and analyzing the breach to recommend security enhancements. |
| Legal and Compliance Notifications | Notify the appropriate authorities and comply with legal requirements for breach reporting. This may include informing local law enforcement and following specific protocols in your jurisdiction for notifying affected individuals and possibly public announcements. |
| Communicate Transparently | Inform all stakeholders, including employees, customers, and partners about the breach. Maintain transparency about what occurred and the steps being taken to address the issue. Avoid withholding information that could help stakeholders protect their own data. |
Long-term Precautions
To prevent future incidents and restore trust, consider the following long-term strategies:
– Review and Enhance Security Measures: Analyze the incident to identify and rectify security lapses. Enhance physical and digital security measures to guard against future breaches.
Continuous Monitoring and Training: Implement ongoing monitoring of your systems. Regularly update your security protocols and train employees on security best practices to recognize and respond to cyber threats.
Build a Responsive Plan: Develop a comprehensive incident response plan that includes immediate actions, communication strategies, and recovery processes. This ensures preparedness for potential future breaches.
By following these guidelines, organizations can not only respond effectively to data breaches but also fortify their defenses against future threats.
Conclusion
Ultimately, the journey toward enhanced digital security is both ongoing and dynamic, reflecting the evolving landscape of cyber threats and technological advancements. The collective responsibility to protect personal data not only strengthens individual security but also reinforces the foundation of trust and reliability fundamental to the digital community. As we continue to chart the path forward, let us remain committed to the principles of vigilance, integrity, and continuous learning in our quest to safeguard our digital identities.
FAQs
What constitutes a digital identity and what measures can be taken to protect it?
A digital identity comprises the personal data that identifies you online. To protect this identity, consider the following strategies:
– Guard your social security number carefully.
– Use security software that updates itself automatically.
– Store data on an external drive.
– Opt for encrypted internet connections.
– Create strong, secure passwords.
– Be cautious about downloading apps.
– Engage in safe social media practices.
Why is safeguarding your online identity and personal data crucial?
Protecting your online identity and personal data is essential to prevent misuse by third parties, which can lead to phishing scams and identity theft. Effective data protection also helps thwart cybercrimes by securing sensitive information, such as banking details and contact information, from fraudulent activities.
Is it necessary to have digital identity protection?
Yes, digital identity protection is necessary because your digital and physical identities are interconnected. Cybercriminals can exploit this overlap to commit identity theft, invade your privacy, impersonate you for financial gain, or damage your reputation.
What are some effective ways to protect personal information?
To protect your personal information, ensure that all your devices, including computers and smartphones, are password-protected. Only download software and apps from trusted sources. Keep your operating system, antivirus, anti-spam, and firewall programs up to date. Additionally, be cautious when connecting to public networks.