
Who is Responsible for Keeping Personal Data Safe? | A Comprehensive Guide
Who is ultimately responsible for keeping personal data safe? The answer lies in three key roles: the Data Protection Officer (DPO), Data Controller, and Data Processor. Each role is distinct in ensuring compliance with data protection laws such as the General Data. Protection Regulation (GDPR) and protecting the rights of individuals whose data is being processed.
Understanding the differences between these roles is essential for organisations that process personal data. While the DPO is a specific position within a company responsible for overseeing compliance, Data Controllers and Processors are defined by what they do with personal data – whether they determine the purposes of data processing or carry it out on behalf of another party.
Understanding the Key Roles in Data Protection
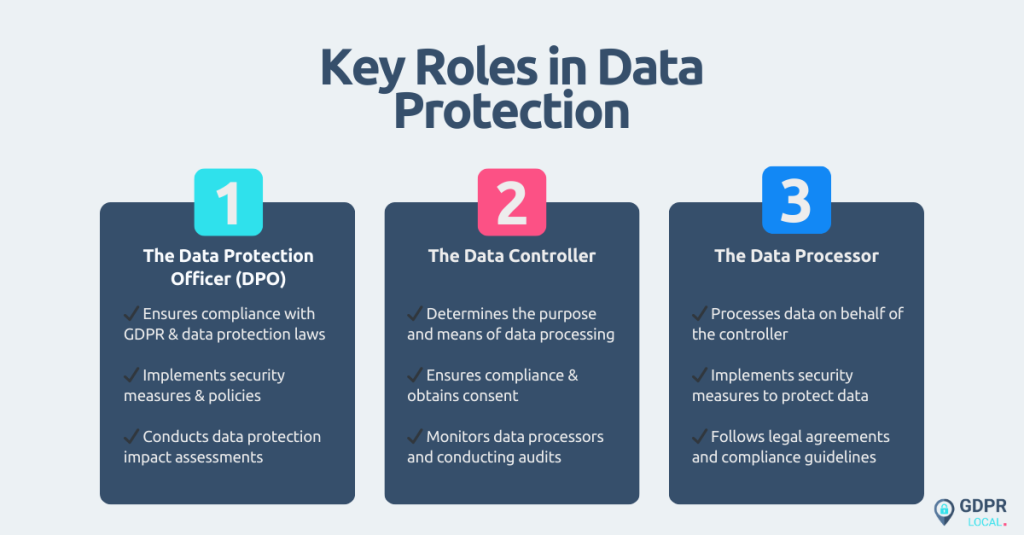
Adequate data protection depends on a clear distinction between the roles of Data Protection Officers (DPOs), Data Controllers, and Data Processors. While the DPO is an appointed individual within an organisation, the Data Controller and Data Processor are roles that describe what an entity (organisation or individual) does with personal data.
The Data Protection Officer (DPO)
The Data Protection Officer (DPO) is a key figure in organisations that need to ensure compliance with GDPR and other data protection regulations. Unlike Data Controllers or Processors, the DPO does not directly determine how data is processed but acts as an independent advisor and compliance officer within an organisation.
Under GDPR, appointing a DPO is mandatory for organisations that:
• Process large-scale sensitive personal data, such as health records or biometric data.
• Engage in systematic monitoring of individuals, including online tracking.
• Public authorities or organisations that regularly process personal data.
The DPO ensures that an organisation sticks to data protection laws. Their responsibilities include:
• Overseeing the implementation of data protection policies.
• Conducting Data Protection Impact Assessments (DPIAs) to identify potential risks.
• Acting as the primary point of contact for data protection authorities.
• Ensuring that employees are trained and aware of data protection obligations.
Although the DPO is a designated position, it must operate independently and cannot be instructed to act in a way that undermines GDPR compliance. The DPO serves as an internal watchdog, ensuring an organisation’s data processing activities meet legal requirements.
The Data Controller: Defining the Purpose and Means of Data Processing
A Data Controller is an organisation or individual that decides why and how personal data is processed. Unlike the DPO, which is a position within an organisation, the Data Controller is a role that defines an entity’s responsibilities regarding data processing.
For example, if a company collects customer data for marketing purposes, it acts as a Data.
Controller because it determines:
• Why the data is collected (e.g., for customer engagement).
• How the data is processed (e.g., stored in a database and used for email marketing).
The Data Controller is primarily responsible for ensuring data processing complies with GDPR. This means they must:
• Obtain valid consent from individuals before processing their data.
• Ensure data processing is lawful, fair, and transparent.
• Implement security measures to prevent data breaches.
• Monitor any Data Processors they engage with to ensure compliance.
A Data Controller can be an organisation or an individual who determines how personal data is processed. However, if an individual processes data for personal or household purposes, such as keeping a private contact list, they are not considered a Data Controller under GDPR.
The Data Processor: Carrying Out Data Processing on Behalf of the Controller
A Data Processor is any organisation or individual that processes personal data on behalf of a Data Controller. Unlike a Controller, a Processor does not decide why or how the data is processed—they only handle data based on the Controller’s instructions.
For example, suppose a company hires an email marketing agency to send promotional emails to customers. In that case, the agency acts as a Data Processor because it processes customer data as the Data Controller instructs.
Responsibilities of a Data Processor include:
• Following the Data Controller’s instructions and not using the data for any other purpose.
• Implementing security measures to protect personal data from breaches.
• Assisting the Data Controller in GDPR compliance, such as conducting audits.
Like Data Controllers, Data Processors can be both organisations and individuals. For instance, an independent IT consultant who manages customer databases for a company would be classified as a Data Processor.
Organisational Measures for Data Protection
An internal policy outlining data protection rules ensures consistent understanding among all staff. Organisational measures prepare for handling data breaches, maintaining operations, and building a culture of data privacy. These measures include conducting information risk assessments, establishing security policies and procedures, and implementing employee training and awareness programs.
These measures align privacy objectives with broader business goals, enhancing overall data management. Here are the specifics of these measures.
Information Risk Assessments
Identifying potential threats to personal data security is crucial for practical risk assessments. Organisations must evaluate the severity and likelihood of identified risks during these assessments. Assessing personal data’s risk, value, and sensitivity helps determine potential damage and appropriate security measures.
These risk assessments help organisations prioritise their resources and implement measures that mitigate the most significant risks. Regular assessments keep the organisation vigilant and prepared for new and evolving data security threats.
Security Policies and Procedures
Security guidelines clarify employees’ responsibilities regarding data protection. Security policies should be documented and readily accessible to all employees involved in data handling. Senior management must actively demonstrate their commitment to data privacy by prioritising it in organisational goals and policies.
Regularly updating data protection policies and practices and adapting them to technological and regulatory changes. This proactive approach ensures compliance with data protection legislation and maintains robust data security while adhering to data protection law.
Employee Training and Awareness
Ongoing training programs ensure employees understand their roles in maintaining data privacy. Staff should receive both initial and refresher training regarding data protection. Employees must realise data protection to safeguard personal data and implement security policies effectively.
A key factor for practical staff training is that trainers must be reliable and knowledgeable. Comprehensive training programs foster a culture of security awareness, ensuring all employees handle personal data responsibly.
Technical Measures for Data Security
Technical measures protect personal data from breaches. According to the GDPR, organisations must adopt appropriate technical and organisational measures to ensure the security of personal data. These measures include implementing access controls, encryption, pseudonymisation, and regular security testing.
Integrating technical measures with organisational policies creates a robust data protection framework addressing physical and IT security. Let’s explore further the specific technical measures that organisations should implement.
Access Controls
Role-based access control limits access based on specific organisational roles and responsibilities. Access controls are essential for protecting personal data, ensuring that only authorised individuals can access sensitive information. Restricting access according to predefined roles reduces the risk of unauthorised access and data breaches.
Robust access controls safeguard personal data and ensure compliance with data protection regulations. These controls help ensure that data is only accessible to those who need it for their work, thereby enhancing data security.
Encryption and Pseudonymisation
Encryption is a widely recommended practice for safeguarding personal data, especially during transmission. Encryption converts data into a coded format, making it unreadable to unauthorised users. This protects data from unauthorised access and breaches during transmission or storage.
Pseudonymisation enhances data security by replacing identifiable information with pseudonyms. This adds an extra layer of protection, ensuring that even if data is accessed unlawfully, it cannot be easily linked to specific individuals. Encryption and pseudonymisation are vital for data protection compliance.
Regular Security Testing
Organisations must regularly assess the effectiveness of their security measures using various testing methods. Vulnerability scanning and penetration testing are key methods to evaluate security. These tests help identify potential weaknesses and vulnerabilities in the system that attackers could exploit.
The frequency of testing security measures varies depending on the organisation and the personal data processed. Regular security testing keeps the organisation’s defences robust and capable of protecting personal data from evolving threats.
Legal and Regulatory Compliance
The General Data Protection Regulation (GDPR) aims to protect the privacy of EU residents’ data, making compliance essential for organisations handling such data. Maintaining GDPR compliance requires adopting best practices for data protection and implementing these privacy measures. Failure to comply with GDPR requirements can result in significant fines and reputational damage.
The GDPR’s influence has been seen globally, with many countries adopting similar data protection legislation. Understanding GDPR requirements, conducting Data Protection Impact Assessments (DPIAs), and demonstrating compliance ensure regulatory standards are met.
Understanding GDPR Requirements
Secure processing of personal data prevents unauthorised access and accidental loss. Organisations must monitor themselves daily for GDPR compliance. This involves implementing appropriate security measures, maintaining accurate records of data processing activities, and ensuring that data subjects’ rights are respected. Additionally, each organisation must process personal data according to the established guidelines to avoid unauthorised or unlawful processing.
Compliance with GDPR requires understanding its requirements and committing to ongoing monitoring and improvement. Adhering to GDPR protects personal data and maintains customer and stakeholder trust.
Data Protection Impact Assessments (DPIAs)
Data Protection Impact Assessments (DPIAs) help organisations identify and minimise data protection risks. DPIAs are mandatory for processing and are likely to result in high risks to individuals’ rights and freedoms. The Data Protection Officer (DPO) provides guidance on conducting DPIAs and ensures compliance with data protection regulations.
DPIAs provide evidence of risk management and demonstrate compliance with GDPR requirements. Conducting DPIAs allows organisations to address potential data protection issues and mitigate risks proactively.
Demonstrating Compliance
Approved codes of conduct or certification schemes help organisations demonstrate compliance with data protection laws. They offer a structured approach to compliance, ensuring regulatory requirements and high data protection standards are met.
Organisations can demonstrate compliance with data protection laws through various methods, ensuring that they meet regulatory requirements. Adhering to these standards builds trust with customers and stakeholders, showing commitment to protecting personal data.
Handling Data Breaches
Effective data breach management minimises harm and meets legal requirements under GDPR. Organisations need clear protocols for detecting, investigating, and reporting data breaches to minimise legal repercussions and safeguard individuals. A strong culture of data privacy within an organisation helps protect personal information and minimise the risk of data breaches.
Data breach management includes identifying them, reporting them promptly, and mitigating their impact. These aspects are explored in more detail below.
Identifying a Data Breach
Data breaches can be classified into several types, including intentional breaches, unintentional breaches, and breaches resulting from technical failures. Intentional breaches include hacking, phishing, and insider threats, while unintentional breaches result from human errors or negligence. Data breach indicators include unusual network activity, unauthorised data access, or employee reports about lost data.
Organisations should foster a culture of vigilance, encouraging employees to report suspicious activity that indicates a data breach. Categorising data breaches helps assess their impact and determine appropriate response actions.
Reporting Obligations
To comply with GDPR, data breaches must be reported to the Information Commissioner’s Office (ICO) within 72 hours. Under GDPR, breaches posing significant risks to individuals’ rights must be reported within this timeframe. This reporting obligation ensures that the authorities know the breach and can take appropriate action to mitigate its impact.
Affected individuals must be notified if a breach likely results in a high risk to their rights and freedoms. This transparency helps individuals take necessary precautions to protect themselves and builds trust in the organisation’s commitment to data protection.
Mitigating Impact
Effective communication strategies inform the public and manage perceptions following a data breach. Organisations should communicate transparently with affected individuals and outline protective steps to mitigate the effects of a data breach. This approach not only helps in managing the immediate impact but also supports the organisation’s reputation in the long term.
Enhancing security protocols and providing support to affected individuals are vital steps to mitigate the impact of a data breach. Organisations can demonstrate their commitment to protecting personal data and minimising harm by taking these actions promptly and efficiently.
Creating a Culture of Data Privacy
Engaging executive leadership to prioritise privacy considerations fosters a thriving data privacy culture. Encouraging a culture of data privacy involves integrating privacy considerations into daily operations and decision-making processes. Regular updates on data protection procedures enhance employee awareness of their roles in safeguarding data.
Building a data privacy culture aligns privacy objectives with business goals and enhances data management. Critical aspects of leadership commitment and continuous improvement are key to creating this culture.
Leadership Commitment
Senior management’s commitment to data privacy can significantly influence the organisation’s overall approach to privacy practices. Leadership prioritising data privacy influences the entire organisation, promoting accountability and responsible data handling. Leadership endorsement of data privacy initiatives sets a precedent, and fosters shared values throughout the organisation.
Senior management actions are vital in cultivating a data privacy culture throughout the organisation. Leadership commitment ensures data protection becomes a fundamental aspect of the organisation’s ethos.
Continuous Improvement
Regularly assessing and enhancing data protection practices allows organisations to adapt to evolving technological and regulatory landscapes. Ongoing enhancement of data protection practices will enable organisations to adapt to new technologies and regulatory requirements.
Continuously improving data protection measures ensures compliance with legislation and maintains high data security standards. This proactive approach helps organisations stay ahead of threats and maintain stakeholder trust.
Summary
Data protection is a multifaceted responsibility shared among different organisational stakeholders. Key roles such as the Data Protection Officer, Data Controller, and Data Processor are crucial in ensuring compliance with data protection regulations. Organisational and technical measures and legal and regulatory compliance are essential for safeguarding personal data. Effective management of data breaches and fostering a culture of data privacy further enhance an organisation’s data protection framework. Organisations can protect personal data, maintain compliance, and build trust with their stakeholders by prioritising data protection.
Frequently Asked Questions
Who is ultimately responsible for protecting personal data?
As the Data Protection Policy outlines, everyone in an organisation is responsible for protecting personal data. This collective accountability ensures that all individuals who handle personal data contribute to its safety and compliance.
Who is responsible for keeping customer data safe?
Everyone involved in processing personal data is responsible for keeping customer data safe. It is vital to uphold this trust by implementing robust security measures.
Who is responsible for data protection in an organisation?
The responsibility for data protection in an organisation is shared among the Data Protection Officer, Data Controller, and Data Processor. Each role plays a critical part in ensuring compliance and safeguarding personal data.
What are the key roles in data protection?
The key roles in data protection are the Data Protection Officer (DPO), Data Controller, and Data Processor, each tasked with specific responsibilities to ensure compliance and protect data. Understanding these roles is vital for effective data governance.
What organisational measures can be taken to protect data?
Organisations should conduct information risk assessments, establish strong security policies, and implement comprehensive employee training programs to protect data effectively. These measures collectively enhance data security and raise awareness across the organisation.