
Handling Breaches in Accordance with PIPEDA
Ensuring compliance with PIPEDA (Personal Information Protection and Electronic Documents Act) is paramount for any company handling personal data.
One of the cornerstones of PIPEDA compliance is having a data breach response procedure in place. Such a procedure serves as a blueprint for companies to effectively address data breaches, ensuring that any potential risks to individuals’ rights are promptly mitigated. In this blog, we’ll delve into the essential steps that companies should take to recognize, record, and respond to data breaches in accordance with PIPEDA guidelines. From establishing internal policies to notifying affected individuals, we’ll explore the critical components of a comprehensive breach response strategy.
What is a Breach of Security Safeguards?
Before we go into detail we need to understand what is considered a breach of security safeguards under PIPEDA.
A breach of security safeguards is defined in PIPEDA as “the loss of, unauthorized access to or unauthorized disclosure of personal information resulting from a breach of an organization’s security safeguards that are referred to in Schedule 1 of PIPEDA, or from a failure to establish those safeguards”.
The safeguards specified in Schedule 1 of PIPEDA consist of the following:
– Safeguards should protect against loss, theft, unauthorized access, disclosure, copying, use, or modification, regardless of the information’s format.
– The level of protection should vary based on the sensitivity of the information.
– Safeguards may include physical, organizational, and technological measures.
– Employees should be made aware of the importance of maintaining confidentiality.
– Care must be taken in the disposal or destruction of personal information to prevent unauthorized access.
Based on the above, a breach of security safeguards encompasses instances of personal information loss, unauthorized access, or unauthorized disclosure due to either a breach of the organization’s security measures or a failure to implement these safeguards.
Organizations Obligations to Report a Breach
When it concerns reporting breaches under PIPEDA, not all incidents mandate reporting to the Office of the Privacy Commissioner (OPC). Nonetheless, if there’s a reasonable belief that a breach of security safeguards presents a genuine risk of significant harm (RROSH) to an individual, it should be reported, irrespective of whether it impacts a single person or many.
The responsibility for reporting rests with the organization managing the personal information implicated in the breach. Although the term “control” lacks an explicit definition, it typically refers to the organization that has transferred personal data to a third party for processing. In such instances, the principal organization is considered to be in control and is accountable for breach reporting. This highlights the significance of having well-defined contractual agreements with third-party processors to ensure adherence to breach reporting requirements. Ultimately, each circumstance must be evaluated individually, considering contractual arrangements and commercial realities. Entities handling personal data on behalf of others also bear responsibilities under PIPEDA, stressing the importance of careful management of personal information.
How to Determine if There is a Real Risk of Significant Harm (RROSH) to an Individual?
When assessing whether a breach of security safeguards poses a real risk of significant harm (RROSH) to an individual, it’s crucial to consider both the sensitivity of the personal information involved and the probability that it has been, is being, or will be misused. Sensitivity can vary depending on the context and includes factors like health and financial information, as well as ethnic, racial, political, genetic, biometric, sexual, and religious beliefs. The circumstances surrounding the breach can also influence sensitivity and potential harm.
To gauge the probability of misuse, several questions should be considered, such as the likelihood of harm resulting from the breach, who accessed or could access the information, how long it was exposed, and whether there’s evidence of malicious intent like theft or hacking. Additionally, factors like the number of breached pieces of information, the entities involved, and whether harm has already occurred should be assessed.
To decide if a breach needs reporting and how to protect privacy, organizations must create a clear method. This involves looking at what information was breached, the situation, and the potential for harm. By doing this carefully, they can decide if reporting is necessary and take steps to prevent harm and safeguard people’s privacy.
Keeping Records
Under PIPEDA, organizations are required to maintain records of all breaches of security safeguards involving personal information under their control, regardless of whether there’s a real risk of significant harm. These records should include key details such as the date of the breach, circumstances, nature of information involved, and whether the breach was reported. While records should describe the nature of the breached information, they need not include personal details unless necessary.
Records must be kept for a minimum of two years to comply with legal requirements, though additional obligations may necessitate longer retention periods.
Notifying Individuals About a Breach
When it comes to notifying individuals about data breaches, there are several important factors to consider. Here’s what you need to know:
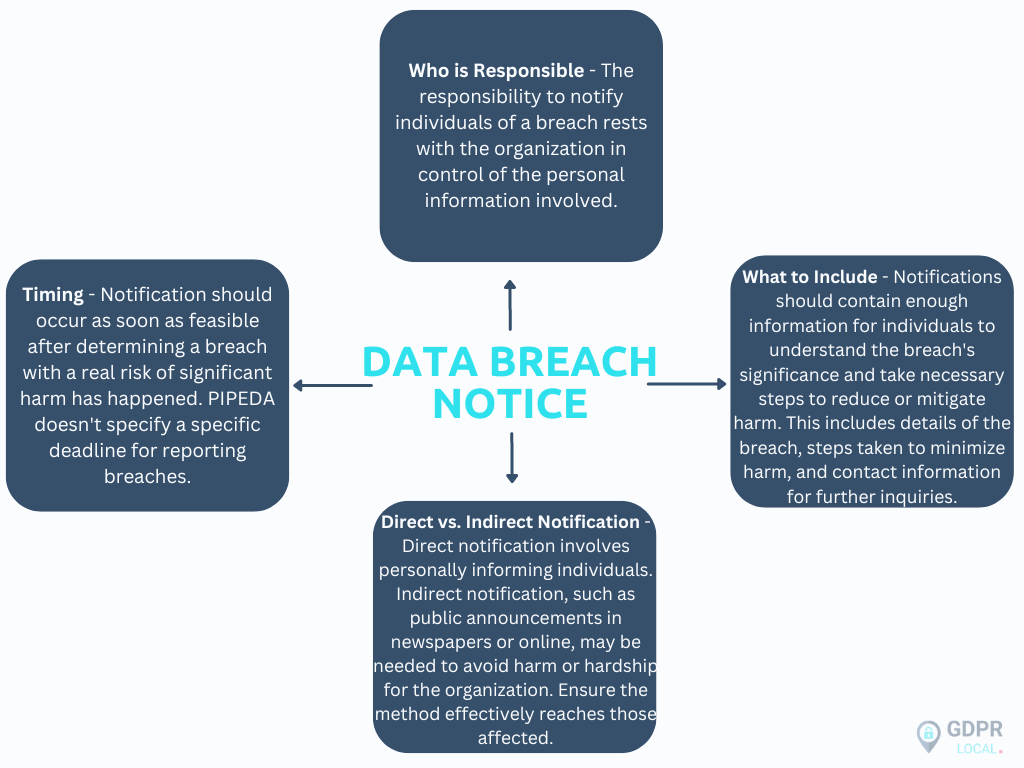
Remember, transparency and clarity are key when notifying individuals about data breaches. By following these guidelines, organizations can fulfil their obligations and help individuals protect their privacy and mitigate potential harm.
Notifying Organizations About a Breach
In the event of a data breach involving a real risk of significant harm, it’s not just individuals who need to be notified. The same organization that notifies the individuals about the breach is also responsible for informing relevant government institutions or other organizations that can help mitigate the potential harm. Here’s what you should keep in mind:

Every situation is different, and the particular organizations or institutions to notify will differ based on the scenario. Nonetheless, the main objective remains consistent: to inform all relevant parties to reduce the breach’s impact on affected individuals as much as possible.
What You Can Do to Ensure Compliance
Develop a Breach Response Plan
Create a detailed plan outlining the steps to take in the event of a data breach. This plan should include protocols for assessing the breach, determining the extent of the impact, notifying affected individuals and authorities, and mitigating harm.
Establish Reporting Procedures
Clearly define the process for reporting breaches internally within the organization. Ensure that all employees know who to report breaches to and the timeline for doing so.
Train Employees
Provide training to all staff members on how to recognize, report, and respond to data breaches. This should include understanding their roles and responsibilities in the event of a breach and the importance of prompt reporting.
Record Keeping
Keep detailed records of the data breach, including the date and nature of the breach, actions taken in response, communications with affected individuals and authorities, and any remediation efforts. Documentation is crucial for demonstrating compliance with breach reporting requirements.
How Can We Help?
With data breaches becoming more common and privacy regulations like PIPEDA gaining importance, it’s crucial for organizations to be proactive in protecting their data and reputation. Our consultants can help create tailored policies to manage data breach requests effectively, ensuring PIPEDA compliance while improving your ability to respond quickly and accurately. Taking this proactive approach can reduce the risk of non-compliance, minimize the impact of breaches, and build trust with customers and stakeholders.